Wednesday, May 18, 2011
Hack Blogger
Here's the link for your perusal.
http://www.nirgoldshlager.com/2011/03/blogger-get-administrator-privilege-on.html
DDoSing Tumblr

DDoSing Tumblr. This site frequently goes down. I myself am guilty of sitting there and hitting F5 over and over again until it pops up.
Firesheep, Protect Yourself
In my last post, I talked about a new firefox extension called firesheep and how it can steal your logon sessions from websites like facebook. While visiting your local starbucks, or using your schools public wifi, who knows if there is someone else running firesheep on it. I’m curious to stop by the starbucks near my college and do some shoulder snooping. How much do you want to bet I’ll find someone running it?
While using a public wifi, if your only doing things like reading the news, then you don’t have to worry. It’s the people who are logging into various online services that have to worry. The best protection against someone using firesheep, is to not use public wifi or to avoid logging into sites. But this sucks, and that’s facebook (don’t know why i keep picking on facebook, lol) is probably 90% of the reason your even using the public wifi.
If you choose to continue using the public wifi, and want to log into your various accounts, the 1st method of protecting yourself is to use a VPN (virtual private network). Those of you who work from home (or starbucks!) you probably use a VPN to log into your workplaces network. VPN is good because it “tunnels” or encrypts data between your computer and the server running the VPN. Your cookies will be safe from anyone at the coffee shop, and so will all of your browsing habits. The downside of VPN is that if you don’t already have one set up, you have to pay per month for it. This could range between $7-$50 dollars a month. There are also ways to set up one on your home computer, but that’s for another posting.
The 2nd way of protecting yourself, is totally free, and that’s to force the website to use SSL on everything. You can do this easily by using some firefox extensions, like Force TLS and Facebook Secure. Unfortunately there is nothing out for IE or Chrome at the moment, but hopefully this simple attack will spur them into creating some way of forcing SSL connections on sites you specify.
Hopefully we will start to see sites providing some sort of encryption for everything and not just the login. For now though, at least you have some ways of protecting yourself.
VPN:
Extensions:
Hacking a Password Protected Iphone
For those who may or may not know, it’s possible to setup a password on your iphone. This way, if someone gets their hands on your phone, they wont have access to any of your information. Now a way to bypass that password has surfaced. By pressing certain things in sequence on the emergency call screen, a thief can gain access to all of your contacts, voicemails, and history. They don’t get access to the rest of the phone, but I think we can agree that your contacts and voicemails are most important to keep private.
Below is the video I found in a link on twitter. Go ahead and try the hack on your own iphone, I did :) If you get stuck and can’t back out of the screen, just call a phone number and then cancel it. This will send you back to the passcode screen.
—-Update: This trick only works on iphones that are currently up to date. Tried to show a friend yesterday and it didn’t work because their iphone had never even been updated—
[youtube=http://www.youtube.com/v/ugADxS5ol48?fs=1]
Firesheep, Sidejacking Made Easy
Toorcon, a network and computer security conference, was just last weekend. Over the past few days, the internet has gone crazy over a new firefox extension, Firesheep, that was unveiled there. You wont be able to find Firesheep where you typically get all of your firefox extensions, but you can download it on the authors website at http://codebutler.github.com/firesheep/
So why has this extension taken over the internet by storm? And by storm, I mean over 120,000 downloads, and news stories about this tool on every news website I typically visit. Firesheep is a one click, simple (except for some windows users) way to hijack someone’s facebook, twitter, etc. If your on a local wifi, you’re probably susceptible to getting your accounts broken into. This is because most local wifis are unencrypted or at least running WEP (which is also susceptible).
What is sidejacking? Sidejacking is a technique used to gain access to a victims online account without needing to find their username or password. This is made possible by grabbing a users cookie. You have probably heard or seen cookies when cleaning them out in your browser. A cookie is what keeps your signed in to your account. Without it, you would have to keep logging in everytime you visited a different webpage. Cookies are also used with the shopping carts seen on websites; that’s how it remembers what you ordered. So cookies are very useful in the online world. The main problem is that most sites don’t encrypt them. A website, like facebook, will encrypt your login information but will send you the cookie unencrypted. Over a wireless network, it’s just simple prey floating through the air, just waiting for another attacker like firesheep to grab it.
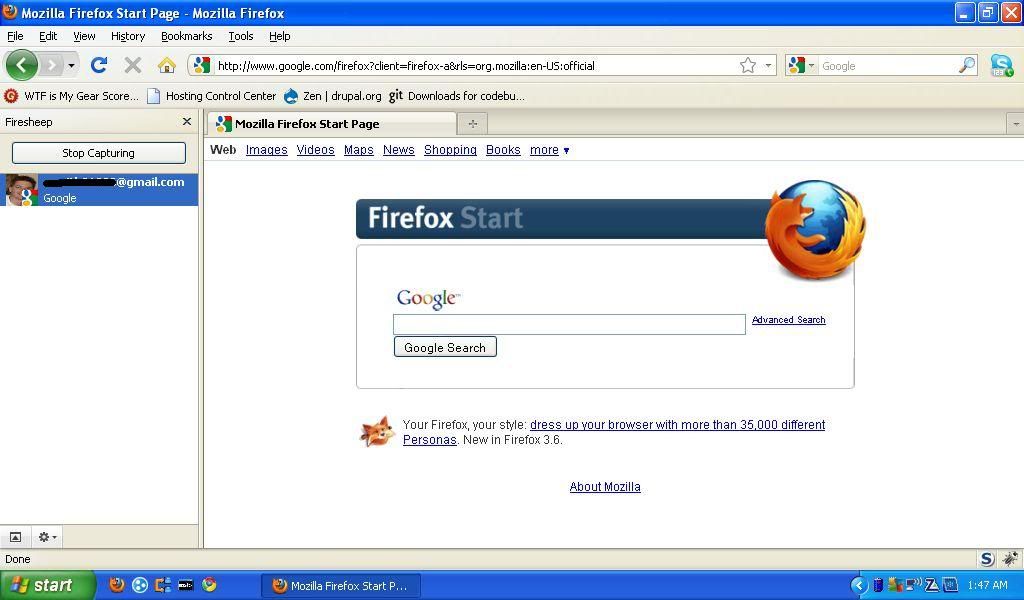 The picture to the right is firesheep in action. Firesheep sits in the bar at the left, and sniffs port 80 (unless otherwise specified) for all of those yummy cookies. As it finds them, it lists the victims name, pic, and what website they’re on. You can double click one of the listed sites, and the session will appear in the window to the right, already open and logged in.
The picture to the right is firesheep in action. Firesheep sits in the bar at the left, and sniffs port 80 (unless otherwise specified) for all of those yummy cookies. As it finds them, it lists the victims name, pic, and what website they’re on. You can double click one of the listed sites, and the session will appear in the window to the right, already open and logged in.
Google is safe, somewhat, against this type off attack. They have actually deployed SSL for everything on their site as of last December. I myself have always been told that running SSL on everything is a complete waste and takes way to much computing power. Google has stated that they only see a 2% increase in CPU usage and feel that everyone should move to using SSL on everything and not just the login. For smaller companies with one server, this is hard, but for big companies like Facebook, Twitter, and Hotmail…. you need to pick up the slack!
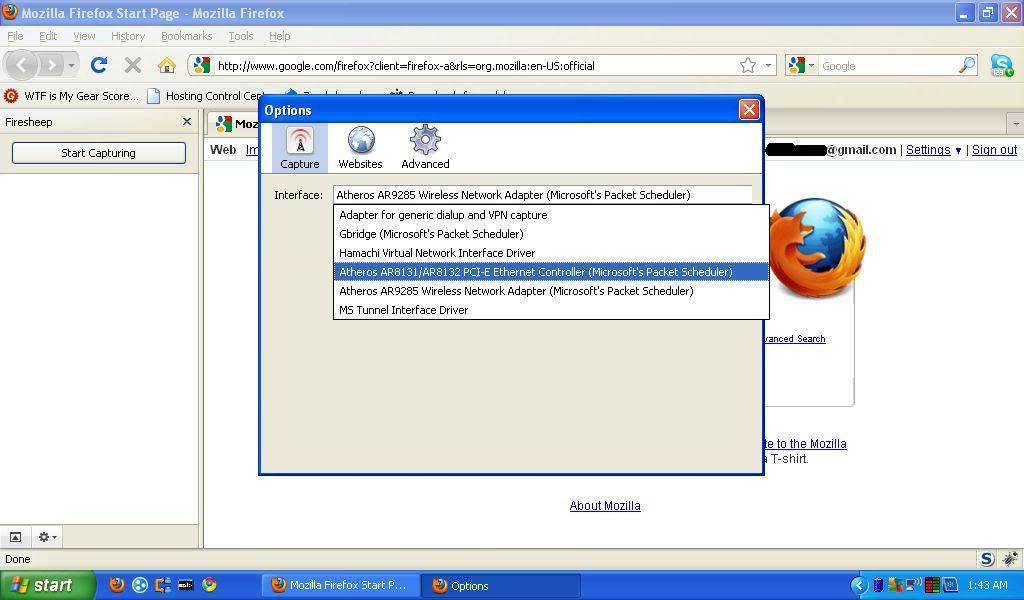 Pictured to the left is the preferences menu inside of Firesheep. You need to specify which device to do the sniffing on. I had some problems myself with the wireless sniffing, mainly due to windows. Your card needs to be put into a passive mode in order to sniff packets. In windows, this is a pain in the butt to do. You have to have winPcap downloaded, but sometimes that doesn’t solve the problem for you. I’m waiting for the linux one myself, so I can load this up into Ubuntu. At least there, it’s possible to put my card into the passive mode.
Pictured to the left is the preferences menu inside of Firesheep. You need to specify which device to do the sniffing on. I had some problems myself with the wireless sniffing, mainly due to windows. Your card needs to be put into a passive mode in order to sniff packets. In windows, this is a pain in the butt to do. You have to have winPcap downloaded, but sometimes that doesn’t solve the problem for you. I’m waiting for the linux one myself, so I can load this up into Ubuntu. At least there, it’s possible to put my card into the passive mode.
If you want to read more on Firesheep, check out the authors website here
Again, you can download it on his website here
You can also download winPcap here
If you’re interested in sidejacking in general. There is another cool tool called Hamster and Ferret. It’s a little more complicated than Firesheep, and requires man in the middle, but it’s another tool to try out.
Thursday, October 22, 2009
SSL (security socket layer)

SSL, what is that? Have you ever noticed while browsing the web, the 's' in https://etc.etc. When the s is sitting there, that means you are using an encrypted connection. So all data you send out to the web server is locked, and the website has the only key to unlock it. This is really nice when doing online banking, as you don't want anyone listening on your network trying to intercept your banking data. If a hacker is on your network, listening to all of your internet traffic, he wont be able to read the data when you are using SSL.
Well there exists a little vulnerability with all web browsers, that can make you think you are secure, while you're actually not. Sometimes a website wont give you the s at the end of the http until you go to login. You may think that's secure because your data is now being encrypted, but that damage has already been done when you visited the site without the s. A hacker can sit between you and the website, a man in the middle, and intercept all data between you and that website. When you first visit the website, you send the request to the hacker, who forwards it onto the website, who then responds back to the hacker, and the hacker forwards the response to you. So when you click that secure login, you actually tell the hacker you want the secure login, who then talks to the website and gets himself a secure login. He/she then spoofs a secure login back to you, so that you are thinking all of your data is being encrypted. But actually, it's as clear as day to the hacker.
So how do you stop a hacker from being the man in the middle? Well, if you had encrypted the data when you first visited the website, he would have never been able to spoof the secure login, and he'll be locked out completely.
So my advice to you, when you visit a website, no matter what site it is, hand type that s at the end of http and press enter. Most websites support SSL, but you'll be surprised how many don't automatically load with it. Gmail doesn't use SSL unless you set in the options that you want it to. Another suggestion of mine to save you from hand typing that s in all the time, is to bookmark the page with the s in it. That way every time you click the bookmark, you automatically go to the page using SSL.
I implore that anyone reading this, whenever visiting a site that contains personal information, or takes a login and password. Especially when you are on a public hot spot, like star bucks. In one day, it has been possible to record as many as 1200 different pieces of personal information off of a public wifi. That was simply a person sitting with a computer running software, that listens to the net chatter. It could have been negated if people would be using the SSL.
Thursday, May 14, 2009
authenticator

Well i have finally added the authenticator to my wow account. No i didn't use one of those keychain ones. blizzard has an app for the iphones that does the same job. I never planned on using the authenticator...but it seems more and more lately that i keep hearing horror stories of people accounts being hacked. more reason to hate gold farmers!!! so as a side note.. any of you buying gold, are only buying someone elses hard work that was stolen from them. back to subject.. i was wrking.. ahem. on photoshop. so that i can start making this blog a little prettier. and i got infected by a trojan. that was the straw that broke the camels back per say.. and now i have that kinda annoying.. xtra protection to my wow account. at least this way i wont have to worry about logging in one day.. to find my characters naked, and all of my gold sold off.