Toorcon, a network and computer security conference, was just last weekend. Over the past few days, the internet has gone crazy over a new firefox extension, Firesheep, that was unveiled there. You wont be able to find Firesheep where you typically get all of your firefox extensions, but you can download it on the authors website at http://codebutler.github.com/firesheep/
So why has this extension taken over the internet by storm? And by storm, I mean over 120,000 downloads, and news stories about this tool on every news website I typically visit. Firesheep is a one click, simple (except for some windows users) way to hijack someone’s facebook, twitter, etc. If your on a local wifi, you’re probably susceptible to getting your accounts broken into. This is because most local wifis are unencrypted or at least running WEP (which is also susceptible).
What is sidejacking? Sidejacking is a technique used to gain access to a victims online account without needing to find their username or password. This is made possible by grabbing a users cookie. You have probably heard or seen cookies when cleaning them out in your browser. A cookie is what keeps your signed in to your account. Without it, you would have to keep logging in everytime you visited a different webpage. Cookies are also used with the shopping carts seen on websites; that’s how it remembers what you ordered. So cookies are very useful in the online world. The main problem is that most sites don’t encrypt them. A website, like facebook, will encrypt your login information but will send you the cookie unencrypted. Over a wireless network, it’s just simple prey floating through the air, just waiting for another attacker like firesheep to grab it.
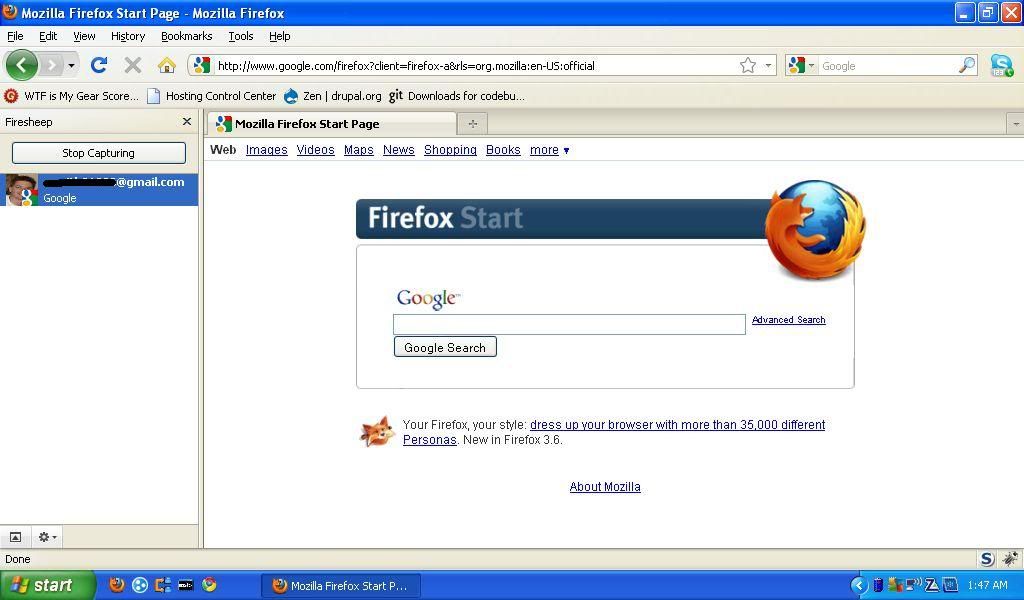 The picture to the right is firesheep in action. Firesheep sits in the bar at the left, and sniffs port 80 (unless otherwise specified) for all of those yummy cookies. As it finds them, it lists the victims name, pic, and what website they’re on. You can double click one of the listed sites, and the session will appear in the window to the right, already open and logged in.
The picture to the right is firesheep in action. Firesheep sits in the bar at the left, and sniffs port 80 (unless otherwise specified) for all of those yummy cookies. As it finds them, it lists the victims name, pic, and what website they’re on. You can double click one of the listed sites, and the session will appear in the window to the right, already open and logged in.
Google is safe, somewhat, against this type off attack. They have actually deployed SSL for everything on their site as of last December. I myself have always been told that running SSL on everything is a complete waste and takes way to much computing power. Google has stated that they only see a 2% increase in CPU usage and feel that everyone should move to using SSL on everything and not just the login. For smaller companies with one server, this is hard, but for big companies like Facebook, Twitter, and Hotmail…. you need to pick up the slack!
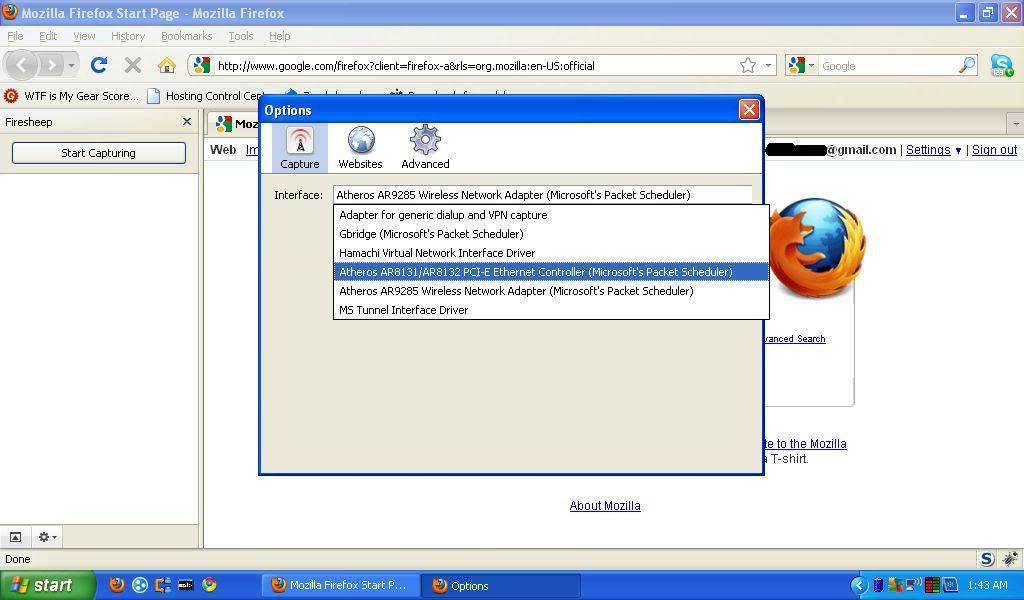 Pictured to the left is the preferences menu inside of Firesheep. You need to specify which device to do the sniffing on. I had some problems myself with the wireless sniffing, mainly due to windows. Your card needs to be put into a passive mode in order to sniff packets. In windows, this is a pain in the butt to do. You have to have winPcap downloaded, but sometimes that doesn’t solve the problem for you. I’m waiting for the linux one myself, so I can load this up into Ubuntu. At least there, it’s possible to put my card into the passive mode.
Pictured to the left is the preferences menu inside of Firesheep. You need to specify which device to do the sniffing on. I had some problems myself with the wireless sniffing, mainly due to windows. Your card needs to be put into a passive mode in order to sniff packets. In windows, this is a pain in the butt to do. You have to have winPcap downloaded, but sometimes that doesn’t solve the problem for you. I’m waiting for the linux one myself, so I can load this up into Ubuntu. At least there, it’s possible to put my card into the passive mode.
If you want to read more on Firesheep, check out the authors website here
Again, you can download it on his website here
You can also download winPcap here
If you’re interested in sidejacking in general. There is another cool tool called Hamster and Ferret. It’s a little more complicated than Firesheep, and requires man in the middle, but it’s another tool to try out.
No comments:
Post a Comment